Security is an essential aspect for any computer network. With so much data now available online, giving ease of access to permitted users, it is important to prevent unauthorised access. Failure to secure a computer network can lead to all sorts of problems for a business, such as data theft, or the network crashing and preventing authorised users from working.
Most computer networks have a firewall, which controls access. A firewall is perhaps the first line of defence in preventing unauthorised access, as it can screen and filter traffic attempting to get on to the network.
All traffic attempting to gain access to the network has to pass through the firewall; however, not all unauthorised attempts to gain access to a network is from people, malicious software is often used to gain access to data or disrupt a compute network, and often these programs can get past this first line of defence.
Different forms of malicious software can gain access to computer networks, and include:
- Computer Viruses and Worms
These can change or replicate existing files and programs. Computer viruses and worms often steal data and send it to unauthorised users.
Trojans appear as harmless software but contains viruses or other malicious software hidden in the program and are often downloaded by people thinking they are normal and benign programs.
Computer programs that spy on the network, reporting to unauthorised users. Often spyware can run undetected for a long time.
A botnet is a collection of computers taken over and used to perform malicious tasks. A computer network can fall victim to a botnet or unwillingly become part of one.
Other threats
Computer networks are attacked in other ways too, such as bombarding the network with access requests. These targeted attacks, called denial-of-service attacks (DDoS attack), can prevent normal use as the network slows down as it tries to deal with all attempts at access.
Protecting Against Threats
Besides the firewall, antivirus software forms the next line of defence against malicious programs. Designed to detect these types of threats, these programs remove or quarantine malicious software before they can do damage to the network.
Antivirus software is essential for any business network and needs regular updating to make sure the program is familiar with all the latest types of threats.
Another essential method for ensuring security is to establish accurate synchronisation of the network. Making sure all machines are running the exact same time will prevent malicious software and users from taking advantage of time lapses. Synchronising to a NTP server (Network Time Protocol) is a common method of ensuring synchronised time. While many NTP servers exist online, these are not very secure as malicious software can hijack the time signal and enter the computer firewall via the NTP port.
Furthermore, online NTP servers can also be attacked leading to the incorrect time being sent to computer networks that access the time from them. A more secure method of getting precise time is to use a dedicated NTP server that works externally to the computer network and receives the time from a GPS (Global Positioning System) source.
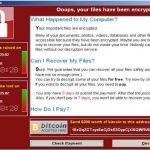


 With a
With a 
 Most computer networks use
Most computer networks use 


